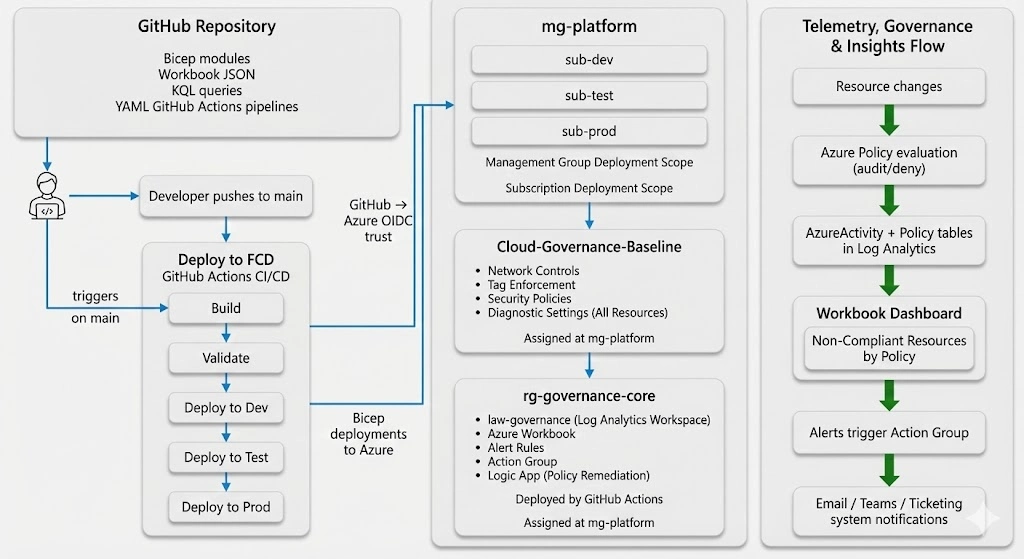
End-to-end mg-platform architecture
The single diagram that explains GitHub, mg-platform, subscriptions and telemetry.
A management group level governance baseline that turns Azure Policy signals into a live compliance system. The Cloud Governance Baseline is deployed once at mg-platform, a standardized "rg-governance-core pattern" is rolled out to every subscription (Dev/Test/Prod), and Log Analytics + Workbooks transform policy telemetry into real-time insights. Alerts flag misconfigurations within minutes, all delivered through a multi-stage GitHub Actions pipeline.

GitHub repo → GitHub Actions CI/CD → mg-platform: Cloud-Governance-Baseline (policies + initiative) → sub-dev / sub-test / sub-prod: rg-governance-core + Log Analytics → Workbook dashboards + alerts → Platform team inbox
Most teams enable a few policies per subscription and stop there. This project treats governance as an engineering product at the management-group level: Bicep-defined policies and initiatives deployed once at mg-platform, rolled out automatically to sub-dev, sub-test and sub-prod via GitHub Actions, and surfaced through a single mg-level Workbook and alerting pattern that works consistently across all environments.
In most Azure environments, each subscription has slightly different policies—often applied manually. There’s no mg-level view, inconsistent alerting and no repeatable mechanism for onboarding new subscriptions into governance
The Cloud Policy Compliance Dashboard defines a Cloud-Governance-Baseline initiative at mg-platform and a rg-governance-core pattern for each subscription. A GitHub Actions pipeline builds, validates and deploys to sub-dev, sub-test, and sub-prod, ensuring the same governance posture is enforced across all environments.
The diagram breaks the platform into three verticals, GitHub CI/CD, mg-platform control plane, and telemetry. Showing how a single push to main rolls out a governance baseline across Dev/Test/Prod and drives a shared mg-level compliance dashboard..
what-if against
the mg-platform and dev subscription templates before any changes are applied.
Cloud-Governance-Baseline initiative, then assigns it at
mg-platform so all child subscriptions inherit the baseline.
rg-governance-core into
sub-dev, sub-test and sub-prod with a Log Analytics
workspace, Action Group, alert rules and Workbook.
The right side of the architecture shows the telemetry pipeline: resource changes, policy evaluations, and DENY events flowing into Log Analytics. Workbook dashboards surface non-compliance, while alert rules drive actionable notifications to platform or security teams.
PolicyResources summarise compliant vs. non-compliant resources across policies, subscriptions and resource groups.AzureActivity captures real time DENY events generated by mg-platform policies.KQL queries power Workbook visuals and shared alert rules reused (and parameterised) across Dev/Test/ProdA visual walkthrough of the mg-platform baseline: the architecture diagram, management group configuration, initiative and assignment, CI/CD pipeline runs, governance resource groups per subscription and the Workbook/alerts that tie it all together.

The single diagram that explains GitHub, mg-platform, subscriptions and telemetry.

Management group view showing sub-dev, sub-test and sub-prod in scope.

The initiative that groups network controls and future NSG/tag/diagnostic policies.

Single assignment at mg-platform so all child subscriptions inherit the baseline.

Multi-stage GitHub Actions run matching the left column of the diagram.

Governance resource group in sub-dev with law-governance workspace.

The same governance pattern rolled out to test and production subscriptions.

Donuts and charts summarising non-compliant resources by policy and environment.

Tabular view showing exactly which resources are failing which policies.

KQL view of DENY events generated by mg-platform policies across all subs.

Final step of the flow: a governance alert landing in the platform team mailbox.
This demo traces a misconfiguration created in sub-dev as it flows through mg-platform evaluation, surfaces inside the Workbook and triggers an actionable alert in the governance mailbox.
This project uses Azure-native services and GitHub Actions to mirror how a platform engineering team would deploy and operate a governance baseline across management groups and subscriptions.
Moving from subscription-level policies to a management-group baseline changes how you design in Azure: governance becomes modular, versioned, tested, and deployed just like application code. You start thinking in terms of platforms not individual subscriptions.